
As explained in another article (https://www.linkedin.com/pulse/how-create-complex-password-dont-forget-mauro-verderosa/), a way to protect our passwords against people who might wish to breach our secrets, it would be to use complex and hard passwords to guess.
Unfortunately, such behavior has some side effects: without a good mnemonic technique, and with so many passwords to remember, it happens frequently to write the passwords on a paper and to hide it under the keyboard, in the wallet, or to leave clearly visible on a post-it close to the desk accessible to anybody.

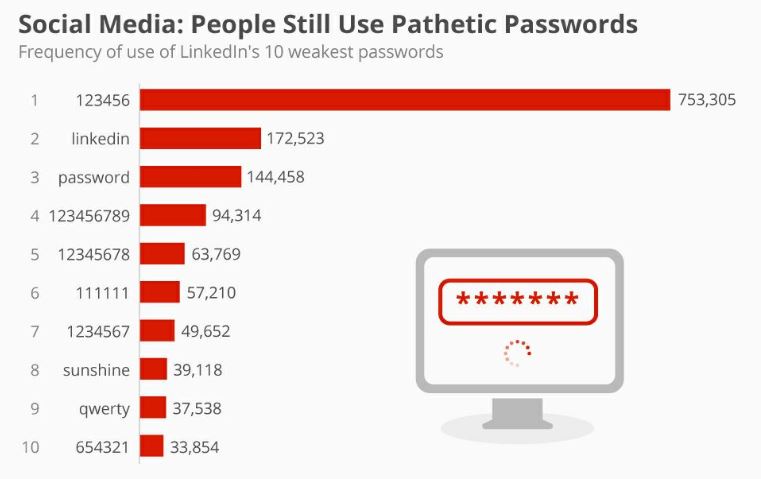
Such bad habits are usually accompanied by using the same password, although complex, for any web service used: web portals, web mails, social networks, etc. This means that if one of these services might be attacked, those got access, for example to the credentials of your social network, will get automatically access also to your email, or to all your online life.
Many people are asking: “which is the best way to create different complex keys for any service, but at the same time to store them in a simple and safe way?”. For our luck the “Password Managers” where invented. A password manager is an application that manages small databases (normally files), that are built with the specific goal of collecting and protecting passwords. At the same time, the access to this application should be controlled by a “Master Password”, a password able to control all the others, a little bit like in “Lord of the Ring”, where the ring of Sauron was able to control all the others.
Because of the criticality of this password, we need to select one really complex, that should be never being transcript, but only memorized.
Now that we know what a password manager is, we need to decide which to use. The market offers us free or commercial solutions. The free ones are ideal for those who might want to use it on their private device. The most known is KeePass. Such databases are thought to stay in your laptop and not to be stored in a Dropbox, Google Drive or other file services or in an email. This is because such applications don’t have a proper access control controlled by an external identity provider. This means that if someone might get access to our database, using the proper tools, he could break the password in no more than a few hours, getting accesses to all your secrets.
In the event that you might prefer to use a cloud access, you could use solutions as LastPass (the most known). In this case the password protection will be outsourced by a third part, and it will be always accessible from every device.
As for many things in life, it doesn’t exist a perfect solution, everything depends by what secrets do you need to protect and by your habits